Good Day Ransomware
Ruining your morning
Overview
The Good day ransomware variant has been on the scene since May 2023. It is unclear if this encryptor is designed for a specific victim or victim region, but it has been tied to the Cloak leak site. The Cloak leaksite has had medium and small sized businesses as victims.
The ransomware note contains a reference to the email 'MikLYmAklY555[@]cock[.]li' which has been associated with other malware families including ARCrypter.
Key points
Deletes the volume shadow copies after it starts encrypting files
Checks for a list of common debuggers in the current running process list
Hardcoded drive letters
Uses libCryptoPP
Multiple encrypted file extensions
Technical Analysis
Hash: 24b1b23b046a0cd196f38ffd6d43b661fbbc2496dc7f67824f1ac16f3e90ccc1 ( VirusTotal )
Entrypoint
Reversed-engineered Source code: Github
The entrypoint of the ransomware starts off by attempting to process command line arguments before executing the bulk of the tactics and techniques to facilitate the encryptor.
Various techniques such as deleting itself, anti-debug, clearing the clipboard, discovering files, removing shadow copies and finally removing traces of itself from disk.
Interesting enough, that the encryptor deletes the shadow copies after the encrypting of the file. A lot of ransomware will attempt to delete shadow copies prior to the encryption process.
Delete self from disk
Reversed-engineered Source code: Github
Mitre: T1070 - Indicator Removal
The function starts off by getting a snapshot of each process in the system, then attempts to iterate through each process by opening it and getting the process ID. The process ID is then compared against the running process.
Once the process handle is found, the fully qualified path is found using the process handle. With the file path found, cmd.exe is executed to delete the file from disk.
/c TIMEOUT /T 2>NUL&START /b "" cmd /c DEL "',0
APIs
- CreateToolhelp32Snapshot
- Process32FirstW
- Process32NextW
- K32GetModuleFileNameExW
- OpenProcess
- PathFindFileNameW
- ShellExecuteW
- TerminateProcess
- ExitProcess
Relaunch debug free
Mitre: T1622 - Debugger Evasion
The anti-debug starts by checking if the IsDebuggerPresent() is set. If it is, a new process is created using the same arguments as the current running process. Once started, the existing process is terminated using a success process return value (zero).
- IsDebuggerPresent
- ExitProcess
- CreateProcessW
Check for process anti-analysis
Reversed-engineered Source code: Github
Mitre: T1622 - Debugger Evasion
The ransomware will attempt to determine if any process that may interfer with the encryptor is running. The anti analysis technique will first get a snapshot of running processes and attempt to compare them to each of the process names in a list.
If found, the sample will use attempt to terminate the process using the exit code 9.
List of Processes:
.data:00479020 processExeList dd offset aSndExe_0 ; DATA XREF: WinMain(x,x,x,x)+36↑o
.data:00479020 ; ProcessFilesEncryption+60↑o
.data:00479020 ; "SND.EXE"
.data:00479024 dd offset aSIceExe_0 ; "S-Ice.Exe"
.data:00479028 dd offset aImmunitydebugg_0 ; "ImmunityDebugger.exe"
.data:0047902C dd offset aX64dbgExe_0 ; "x64dbg.exe"
.data:00479030 dd offset aX32dbgExe_0 ; "x32dbg.exe"
.data:00479034 dd offset aOllydbgExe_0 ; "ollydbg.exe"
.data:00479038 dd offset aWindbgExe_0 ; "windbg.exe"
.data:0047903C dd offset aCdbExe_0 ; "cdb.exe"
.data:00479040 dd offset aSyserx32Exe_0 ; "syserx32.exe"
.data:00479044 dd offset aPdb2sdsx32Exe_0 ; "pdb2sdsx32.exe"
.data:00479048 dd offset aUnpackx32Exe_0 ; "unpackx32.exe"
.data:0047904C dd offset aW32dsm89Exe_0 ; "w32dsm89.exe"
.data:00479050 dd offset aW32dsm88Exe_0 ; "w32dsm88.exe"
.data:00479054 dd offset aW32dsm87Exe_0 ; "w32dsm87.exe"
APIs
- OpenProcess
- CreateToolhelp32Snapshot
- Process32FirstW
- Process32NextW
- TerminateProcess
Clipboard & Delay shutdown
Mitre: T1115 - Clipboard Data
The ransomware process will empty all the data currently in the clipboard buffer, then set the process shutdown parameters to 0. The shutdown priority for the process is set relative to the other processes currently running. The 0 value is setup as the system reserved last shutdown range, and its is intended for system components. The sample does not attempt to set the 'SHUTDOWN_NORETRY' which is used to control if the process should not display a retry dialog box to the user.
APIs
- EmptyClipboard
- SetProcessShutdownParameters
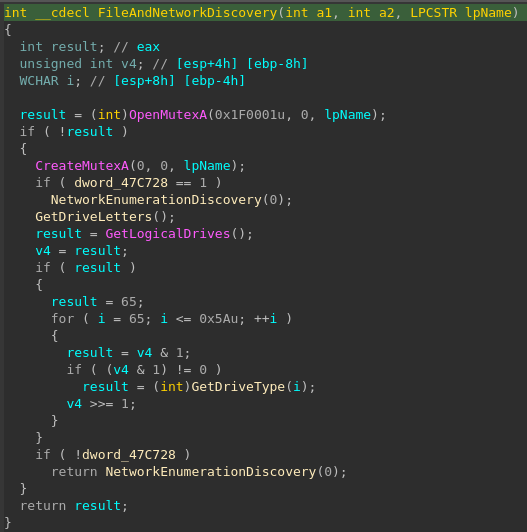
File Discovery and Encryption
Reversed-engineered Source code: Github
Mitre: T1083 - File and Directory discovery
Mitre: T1486 - Data Encrypted for Impact
The file and directory discovery starts off by creating a mutex and a semaphore to ensure that the file discovery and the encryption threads can signal each other. When processing files, the recycle bin is emptied.
The file discovery will use a list of directories and file extensions to filter results and improve discovery time. Note: see notable signals below for a list of directories and file extensions.
The ransomware will discover files and directories locally by obtaining the drive letter and the ensuring the drive type is local or remote but not removables such as a CDROM drive.
Along with local discovery, the ransomware will attempt to enumerate network resources and discovery remote files.
The windows restart manager is used to unlock files from a process during the encryption routine to ensure that the file is successfully encrypted.
The encryption thread will use the AES algorithm and the libCryptoPP to encrypt a file.
The ransomware note is written out into a file called: 'readme_for_unlocks.txt'. Note: see notable signals below for a ransomware note text.
APIs
- CreateThread
- OpenMutexA
- CreateMutexA
- GetLogicalDrives
- WNetOpenEnumW
- WNetEnumResourceW
- WNetCloseEnum
- GetDriveTypeW
- FindFirstVolumeW
- GetVolumePathNamesForVolumeName
- SetVolumeMountPointW
- FindNextVolumeW
- FindVolumeClose
- GetDriveTypeW
- SHEmptyRecycleBinA
- RmRegisterResources
- RmGetList
- RmEndSession
File and directory list
.data:00479058 FileAndDirList dd 0 ; DATA XREF: sub_4178B0+1C↑o
.data:00479058 ; sub_417AB0+32↑o ...
.data:0047905C dd offset aAppdata ; "AppData"
.data:00479060 dd offset aBoot ; "Boot"
.data:00479064 dd offset aWindows ; "Windows"
.data:00479068 dd offset aWindowsOld ; "Windows.old"
.data:0047906C dd offset aTorBrowser ; "Tor Browser"
.data:00479070 dd offset aInternetExplor ; "Internet Explorer"
.data:00479074 dd offset aGoogle ; "Google"
.data:00479078 dd offset aOpera ; "Opera"
.data:0047907C dd offset aOperaSoftware ; "Opera Software"
.data:00479080 dd offset aMozilla ; "Mozilla"
.data:00479084 dd offset aMozillaFirefox ; "Mozilla Firefox"
.data:00479088 dd offset aRecycleBin ; "$Recycle.Bin"
.data:0047908C dd offset aProgramdata ; "ProgramData"
.data:00479090 dd offset aAllUsers ; "All Users"
.data:00479094 dd offset aAutorunInf ; "autorun.inf"
.data:00479098 dd offset aBootfontBin ; "bootfont.bin"
.data:0047909C dd offset aBootsectBak ; "bootsect.bak"
.data:004790A0 dd offset aBootmgr ; "bootmgr"
.data:004790A4 dd offset aNtuserDatLog ; "ntuser.dat.log"
.data:004790A8 dd offset aThumbsDb ; "thumbs.db"
.data:004790AC dd offset aIconcacheDb ; "iconcache.db"
.data:004790B0 dd offset aNtldr ; "ntldr"
.data:004790B4 dd offset aNtuserDat ; "ntuser.dat"
.data:004790B8 dd offset aD3d9capsDat ; "d3d9caps.dat"
.data:004790BC dd offset aProgramFiles ; "Program Files"
.data:004790C0 dd offset aProgramFilesX8 ; "Program Files (x86)"
.data:004790C4 dd offset aRecycle ; "#recycle"
File Extensions
.data:004790D0 FileExtensionList dd offset aSys ; DATA XREF: sub_4178B0+D8↑o
.data:004790D0 ; sub_417AB0+F5↑o ...
.data:004790D0 ; "sys"
.data:004790D4 dd offset aMsstyles ; "msstyles"
.data:004790D8 dd offset aNomedia ; "nomedia"
.data:004790DC dd offset aTmpefi ; "tmpefi"
.data:004790E0 dd offset aLnk ; "lnk"
.data:004790E4 dd offset aExe ; "exe"
.data:004790E8 dd offset aBat ; "bat"
.data:004790EC dd offset aMsi ; "msi"
.data:004790F0 dd offset aDll ; "dll"
.data:004790F4 dd offset aIni ; "ini"
.data:004790F8 dd offset aDeskthemepack ; "deskthemepack"
.data:004790FC dd offset aDiagcab ; "diagcab"
.data:00479100 dd offset aDiagcfg ; "diagcfg"
.data:00479104 dd offset aDiagpkg ; "diagpkg"
.data:00479108 dd offset aDrv ; "drv"
.data:0047910C dd offset aIcl ; "icl"
.data:00479110 dd offset aIcns ; "icns"
.data:00479114 dd offset aMsc ; "msc"
.data:00479118 dd offset aMsp ; "msp"
.data:0047911C dd offset aCrypt ; "crYpt"
.data:00479120 dd offset aDnt_1 ; "dnt"
.data:00479124 dd offset aCrypta1 ; "crYptA1"
.data:00479128 dd offset aCrypta2 ; "crYptA2"
.data:0047912C dd offset aCrypta3 ; "crYptA3"
Hardcoded drive letters
.text:0040126C aQ: ; DATA XREF: GetDriveLetters+9↓o
.text:0040126C text "UTF-16LE", 'Q:\',0
.text:00401274 aW: ; DATA XREF: GetDriveLetters+13↓o
.text:00401274 text "UTF-16LE", 'W:\',0
.text:0040127C aE: ; DATA XREF: GetDriveLetters+1A↓o
.text:0040127C text "UTF-16LE", 'E:\',0
.text:00401284 aR: ; DATA XREF: GetDriveLetters+21↓o
.text:00401284 text "UTF-16LE", 'R:\',0
.text:0040128C aT: ; DATA XREF: GetDriveLetters+28↓o
.text:0040128C text "UTF-16LE", 'T:\',0
.text:00401294 aY: ; DATA XREF: GetDriveLetters+2F↓o
.text:00401294 text "UTF-16LE", 'Y:\',0
.text:0040129C aU: ; DATA XREF: GetDriveLetters+36↓o
.text:0040129C text "UTF-16LE", 'U:\',0
.text:004012A4 aI: ; DATA XREF: GetDriveLetters+3D↓o
.text:004012A4 text "UTF-16LE", 'I:\',0
.text:004012AC aO: ; DATA XREF: GetDriveLetters+44↓o
.text:004012AC text "UTF-16LE", 'O:\',0
.text:004012B4 aP: ; DATA XREF: GetDriveLetters+4B↓o
.text:004012B4 text "UTF-16LE", 'P:\',0
.text:004012BC aA: ; DATA XREF: GetDriveLetters+52↓o
.text:004012BC text "UTF-16LE", 'A:\',0
.text:004012C4 aS_0: ; DATA XREF: GetDriveLetters+59↓o
.text:004012C4 text "UTF-16LE", 'S:\',0
.text:004012CC aD: ; DATA XREF: GetDriveLetters+60↓o
.text:004012CC text "UTF-16LE", 'D:\',0
.text:004012D4 asc_4012D4: ; DATA XREF: GetDriveLetters+67↓o
.text:004012D4 text "UTF-16LE", 'F:\',0
.text:004012DC aG: ; DATA XREF: GetDriveLetters+6E↓o
.text:004012DC text "UTF-16LE", 'G:\',0
.text:004012E4 asc_4012E4: ; DATA XREF: GetDriveLetters+75↓o
.text:004012E4 text "UTF-16LE", 'H:\',0
.text:004012EC aJ: ; DATA XREF: GetDriveLetters+7C↓o
.text:004012EC text "UTF-16LE", 'J:\',0
.text:004012F4 aK: ; DATA XREF: GetDriveLetters+83↓o
.text:004012F4 text "UTF-16LE", 'K:\',0
.text:004012FC asc_4012FC: ; DATA XREF: GetDriveLetters+8A↓o
.text:004012FC text "UTF-16LE", 'L:\',0
.text:00401304 aZ: ; DATA XREF: GetDriveLetters+91↓o
.text:00401304 text "UTF-16LE", 'Z:\',0
.text:0040130C asc_40130C: ; DATA XREF: GetDriveLetters+98↓o
.text:0040130C text "UTF-16LE", 'X:\',0
.text:00401314 aC: ; DATA XREF: GetDriveLetters+9F↓o
.text:00401314 text "UTF-16LE", 'C:\',0
.text:0040131C aV: ; DATA XREF: GetDriveLetters+A6↓o
.text:0040131C text "UTF-16LE", 'V:\',0
.text:00401324 aB: ; DATA XREF: GetDriveLetters+AD↓o
.text:00401324 text "UTF-16LE", 'B:\',0
.text:0040132C aN: ; DATA XREF: GetDriveLetters+B4↓o
.text:0040132C text "UTF-16LE", 'N:\',0
.text:00401334 aM: ; DATA XREF: GetDriveLetters+BB↓o
.text:00401334 text "UTF-16LE", 'M:\',0
Ransomware Note
.text:00401748 ransomeNote db 9,9,9,9,' > ATTENTION <',0Dh,0Ah
.text:00401748 ; DATA XREF: WriteReadMeNoteFile+35↓o
.text:00401748 ; WriteReadMeNoteFile+41↓o
.text:0040175D db 0Dh,0Ah
.text:0040175F db 'Your network is hacked and files are encrypted.',0Dh,0Ah
.text:00401790 db 9,'Including the encrypted data we also downloaded other confident'
.text:004017D0 db 'ial information:',0Dh,0Ah
.text:004017E2 db 9,'Data of your employees, customers, partners, as well as account'
.text:00401822 db 'ing and',0Dh,0Ah
.text:0040182B db 9,'other internal documentation of your company.',0Dh,0Ah
.text:0040185B db 0Dh,0Ah
.text:0040185D db 'All data is stored until you will pay.',0Dh,0Ah
.text:00401885 db 9,'After payment we will provide you the programs for decryption a'
.text:004018C5 db 'nd we will delete your data.',0Dh,0Ah
.text:004018E3 db 9,'If you refuse to negotiate with us (for any reason) all your da'
.text:00401923 db 'ta will be put up for sale.',0Dh,0Ah
.text:00401940 db 0Dh,0Ah
.text:00401942 db 'What you will face if your data gets on the black market:',0Dh,0Ah
.text:0040197D db 9,'1) The personal information of your employees and customers may'
.text:004019BD db ' be used to obtain a loan or',0Dh,0Ah
.text:004019DB db 9,9,'purchases in online stores.',0Dh,0Ah
.text:004019FA db 9,'2) You may be sued by clients of your company for leaking infor'
.text:00401A3A db 'mation that was confidential.',0Dh,0Ah
.text:00401A59 db 9,'3) After other hackers obtain personal data about your employee'
.text:00401A99 db 's, social engineering will be',0Dh,0Ah
.text:00401AB8 db 9,9,'applied to your company and subsequent attacks will only inte'
.text:00401AF7 db 'nsify.',0Dh,0Ah
.text:00401AFF db 9,'4) Bank details and passports can be used to create bank accoun'
.text:00401B3F db 'ts and online wallets through ',0Dh,0Ah
.text:00401B5F db 9,9,'which criminal money will be laundered.',0Dh,0Ah
.text:00401B8A db 9,'5) You will forever lose the reputation.',0Dh,0Ah
.text:00401BB5 db 9,'6) You will be subject to huge fines from the government.',0Dh,0Ah
.text:00401BF1 db 9,9,'You can learn more about liability for data loss here:',0Dh,0Ah
.text:00401C2B db 9,9,9,'https://en.wikipedia.org/wiki/General_Data_Protection_Regul'
.text:00401C69 db 'ation',0Dh,0Ah
.text:00401C70 db 9,9,9,'https://gdpr-info.eu/',0Dh,0Ah
.text:00401C8A db 9,'Courts, fines and the inability to use important files will lea'
.text:00401CCA db 'd you to huge losses.',0Dh,0Ah
.text:00401CE1 db 9,'The consequences of this will be irreversible for you.',0Dh,0Ah
.text:00401D1A db 9,'Contacting the police will not save you from these consequences'
.text:00401D5A db ',',0Dh,0Ah
.text:00401D5D db 9,9,'but will only make your situation worse.',0Dh,0Ah
.text:00401D89 db 0Dh,0Ah
.text:00401D8B db 'You can get out of this situation with minimal losses',0Dh,0Ah
.text:00401DC2 db 9,'To do this you must strictly observe the following rules:',0Dh,0Ah
.text:00401DFE db 9,9,'DO NOT Modify, DO NOT rename, DO NOT copy, DO NOT move any fi'
.text:00401E3D db 'les.',0Dh,0Ah
.text:00401E43 db 9,9,9,'Such actions may DAMAGE them and decryption will be impossi'
.text:00401E81 db 'ble.',0Dh,0Ah
.text:00401E87 db 9,9,'DO NOT use any third party or public decryption software, it '
.text:00401EC6 db 'may also DAMAGE files.',0Dh,0Ah
.text:00401EDE db 9,9,'DO NOT Shutdown or Reboot the system this may DAMAGE files.',0Dh
.text:00401F1C db 0Ah
.text:00401F1D db 9,9,'DO NOT hire any third party negotiators (recovery/police, etc'
.text:00401F5C db '.)',0Dh,0Ah
.text:00401F60 db 9,9,'You need to contact us as soon as possible and start negotiat'
.text:00401F9F db 'ions.',0Dh,0Ah
.text:00401FA6 db 0Dh,0Ah
.text:00401FA8 db 'Instructions for contacting our team:',0Dh,0Ah
.text:00401FCF db 9,'Download & Install TOR browser: https://torproject.org',0Dh,0Ah
.text:00402008 db 9,'For contact us via LIVE CHAT open our',0Dh,0Ah
.text:00402030 db 9,'> Website: http://<redacted>.onion',0Dh,0Ah
.text:00402084 db 9,'> Login: CLIENT',0Dh,0Ah
.text:00402099 db 9,'> Password: <redacted>',0Dh,0Ah
.text:004020BC db 9,'If Tor is restricted in your area, use VPN',0Dh,0Ah
.text:004020E9 db 9,'If you have any problems with LIVE CHAT you can send a message '
.text:00402129 db 'here:',0Dh,0Ah
.text:00402130 db 9,'> Email: MikLYmAklY555@cock.li',0
Delete Shadow Copies
Reversed-engineered Source code: Github
Mitre: T1490 - Inhibit System Recovery
When deleting the shadow copies, the ransomware will first check if the process is a WOW64 process. If it is, the process will attempt to disable the WoW64 file system redirection. Once disabled, the process will then attempt to launch cmd.exe and use it to launch the vssadmin.exe to delete all shadow copies.
vssadmin.exe delete shadows /all /quietAPIs
- LoadLibraryA
- GetProcAddress
- ShellExecuteW
YARA
/*
MIT License
Copyright 2023 ShadowStackRe.com
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the “Software”), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
*/
rule goodday {
meta:
description = "rule to detect Goodday Ransomware"
author = "ShadowStackRe.com"
date = "2023-10-12"
Rule_Version = "v1"
malware_type = "ransomware"
malware_family = "Gooday"
License = "MIT License, https://opensource.org/license/mit/"
strings:
$strFile_A = "crYptA" ascii wide
$strFile_B = "crYptB" ascii wide
$strFile_C = "crYptC" ascii wide
$strFile_D = "crYptD" ascii wide
$strFile_E = "crYptE" ascii wide
$strFile_F = "crYptF" ascii wide
$strTorInfo = "Download & Install TOR browser" ascii wide
$strReadmeNote = "readme_for_unlock.txt" ascii wide
$strAttention = "ATTENTION" ascii wide
$strHacked = "Your network is hacked and files are encrypted." ascii wide
condition:
all of them
}