FrostyGoop
Industrial control system malware
The FrostyGoop malware attack is part of a series of cyber campaigns targeting Ukraine, particularly in the context of heightened geopolitical tensions. The attack was designed to disrupt critical infrastructure in Ukraine, likely as part of broader efforts to destabilize the country. The attack directly affected apartment buildings by attacking a municipal district energy company.
Modbus background & security
MODBUS TCP is a widely-used industrial protocol that enables communication between devices over Ethernet networks. Originally developed by Modicon (now Schneider Electric) in 1979 for serial communication, the protocol evolved over time to support TCP/IP networking as industries shifted toward modern connectivity solutions. Despite its popularity, MODBUS TCP has inherent security weaknesses. Since it was designed for use in trusted industrial environments, it lacks robust security features such as encryption and authentication. This makes it vulnerable to attacks like eavesdropping, replay, and unauthorized access, as malicious actors can easily connect to, send data or intercept and manipulate data. With the rise of interconnected industrial systems, these vulnerabilities have become more significant, prompting the need for additional security measures or more secure protocols in critical infrastructure.
Low Detection rates
The current FrostGoop samples are well known and AV signatures have been developed since the original attack by all major AV vendors. With that said, at the time of the attack the samples were not triggering detection signatures due to the fact that the binary itself is fairly streamlined. At its core, the malware will: read input files, connect to a well known MODBUS port and send data via a TCP socket. These indicators are not malicious and will easily be over looked by an EDR system when attempting to identify behavior. Because the threat actor decided to forgo the common persistence, obfuscation and evasion mechanisms seen in typical malware, it allowed the attackers to deploy and execute their malware without being interrupted. Due to the lack of anti-analysis techniques, the samples were most likely expected to be a one time attack.
Sha256: 5d2e4fd08f81e3b2eb2f3eaae16eb32ae02e760afc36fa17f4649322f6da53fb
Golang & Third-party libraries
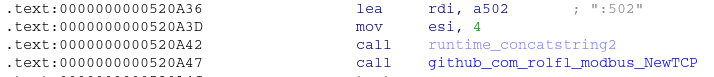
The sample was developed in the Go language and compiled for Windows with two third-party open source libraries. The MODBUS library used was from the github repository github.com/rolfl/modbus, the library is used for interfacing with MODBUS as either a client, or server - either TCP or RTU protocols. This library is not malicious, and was integrated into the sample to shorten the time needed by the threat actor to get a working MODBUS payload. The other facilitates queueing execution tasks which interact with the MODBUS library. The github.com/hsblhsn/queues repository was integrated into the sample with a sync.WaitGroup like queue and goroutine execution controller that limits goroutine executions.
Configuration
A flexible configuration was developed by the attacker. The target IP address, an input task, input target list, and the ability to control what is written to the MODBUS registers makes this malware sample very flexible and re-usable against other MODBUS targets. An output file is used to record the responses received from each task. Each configuration file is in the JSON format and uses the built in Golang JSON marshaller and UnMarshaller functions. This functionality can be found at the main user entry point within the binary at address 0x00000521D00.
MODBUS TCP
TCP Port 502 is a typical port used for MODBUS, but as we mentioned prior, the protocol does not encrypt data or contain any authentication / authorization. The protocol itself contains the concept of "coils" and "registers". These concepts are associated with a general function in a MODBUS system. Register are located at a specific address (like a memory address) and are 16-bits in size. Registers can be read only or write only, and the function it provides at an address (or offset) is dependent on the system that implements the protocol. More on the MODBUS protocol can be found here.
The sample has the ability to write to a single register, read from a single register or multiples (32-bit values are considered more than one register). Since the registers and the values that are written to them are specific to a function, the threat actor must have a deep understanding of the target system to ensure the value triggers the intended outcome.
Command execution is done at address 0x00005202A0 and utilizes common MODBUS structures to interact with the system. An address is required to identify a specific register (or offset), and a 16-bit value is used to writing or reading data.
// Golang representation of the structure
00000000 struct modbus_X03xReadHolding
00000000 {
00000000 signed __int64 Address; // Address of the register
00000008 _slice_int Values; // Read value
00000020 };
00000000 struct modbus_X06xWriteSingleHolding
00000000 {
00000000 signed __int64 Address; // Address of the register
00000008 signed __int64 Value; // Write value
00000010 };Conclusion
Countless ICS based systems running MODBUS are exposed via Shodan everyday.
Shodan - Port 502 open
A successful malware attack on an ICS target could lead to severe disruptions, operational failures, and even threats to public safety. By implementing robust security measures such as authorization, identification, and network segmentation for vulnerable protocols such as the MODBUS TCP protocol, we can protect these vital systems from malicious activity.